23 March 2023
Impulse Offer
Ensuring the security of connected objects and the protection of the data they exchange is becoming a vital issue for many companies. The loss of control over an object or the leaking of private data can quickly lead to dramatic consequences on the credibility of a product or service offering. Manufacturers have an important role to play in order to propose solutions adapted to security and data protection needs.
We interviewed our experts to find out more about the cybersecurity issues behind IIoT.
Why is the need for security higher for connected objects?

Frédéric Piller
Digital Factory R&D Manager, LACROIX
Connected objects are increasingly present in our daily lives
Whether for domestic or professional use, it is estimated that by 2025, 75 billion objects will be connected to the internet. Smart light bulbs, predictive maintenance sensors on production lines, personal data collection systems and the likes are among the smart devices that make use of different network technologies (e.g. 4G, Wi-Fi, LoRa) to process, send, and analyze data.
A growing number of cyber attacks on these objects
In parallel to this growth in the production of connected objects, there is also a growing number of cyber attacks on these objects. Cyber attacks are estimated to have cost 5.5 billion euros. Data theft, taking control of devices, and interruption of services are just a few of many examples.
As an IoT solutions designer, what solutions does LACROIX implement to ensure security for the data of your customers’ connected objects?

Yannick Gaudin
R&D Security Architect, LACROIX
Cybersecurity from the design stage…
Our role is to support our customers in the design of their IoT products by directly integrating cyber security, by:
- Uniquely and safely identifying products
- Authenticating communications with our IoT platforms to ensure the origin of data received and transmitted
- Protecting the integrity and authenticity of our product code to prevent it from being used for malicious purposes
- Continuously updating security protocols to correct flaws, add new features, or renew certificates, for example
- Granting the ability to store confidential data (passwords, private keys)
… and throughout a product’s life cycle
This level of security must be maintained throughout the lifespan of an IoT product, from its design to its recycling, including its production and operation.
Validate the safety of your products with our experts
Focus on the “Secure by design” concept
A “secure by design” product means that risk and security are integrated at the design stage and throughout the product’s lifecycle. Its architecture is designed to be sufficiently robust to guarantee the security and confidentiality of software systems.
Source : Oracle
How does LACROIX support your customers with the « Secure by Design » approach?

Frédéric Piller
Digital Factory R&D Manager, LACROIX
Our product design strategy is based on the “Secure by Design” concept into 5 steps. It is essential to secure the design of your products as far upstream as possible.
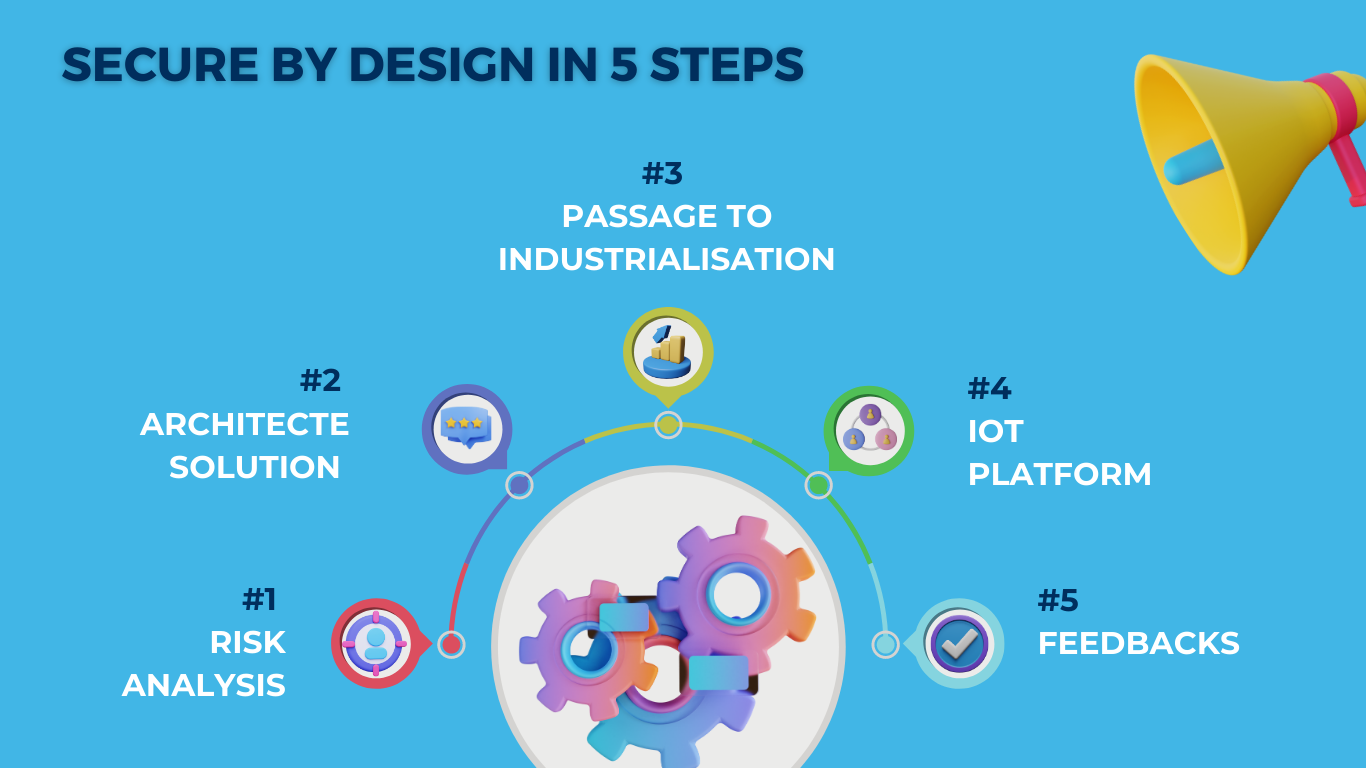
Step #1 : Risk analysis
We support our customers with risk analysis to fully understand the level of security to be implemented depending on the environment in which the product will operate.
Step #2 : Architecture solution
We then define the hardware architecture solution (electronic, mechanical) and software adapted to our customers’ needs. We organize all our practices and processes around cyber security: code reviews, coding rules, crisis management plans, active monitoring of vulnerabilities, etc. These processes allow us to anticipate potential security threats. We address cyber security at the entire system level so as not to leave any weak links that could compromise the whole security chain.
Step #3 : Passage to industrialisation
With the production sites of the Electronics activity of LACROIX, we are fully able to support you with the manufacture of your IoT projects. We make it possible to connect with your PKI (Public Key Infrastructure), or that of LACROIX if you do not have one, in order to ensure solid authentication of products, right from the onset of factory production.
Step #4 : IoT platform
We also offer a generic and secure IoT platform that connects all IoT products produced by LACROIX. This platform has numerous advantages, particularly with regards to data collection and processing, secure firmware updates, certificate renewal, and industrial fleet management (device management).
The development of this IoT platform is at the heart of our “Secure by Design” strategy. Our versatile LX Connect platform offers you a turnkey solution to accelerate your IoT projects.
Discover in video an overview of our IoT platform
Step #5 : Feedbacks
The final stage of our support is characterized by feedback on the overall IoT project. The aim is to listen to the customer’s feedback, and to pursue further developments if necessary.
As we all know, to ensure that an IoT project is secure and its data protected, it’s essential to ask the right questions, respect certain key rules and surround yourself with reliable partners. The sector is evolving very fast, which means keeping a close eye on technological and legal developments, particularly with the arrival of the CRA (Cyber Resilience Act), which is reshuffling the cards in cybersecurity. But that’s another story…
You have an IoT project IoT and you want to talk about cybersecurity? Contact-us!
To know more about security and protecting connected objects
Find out this conference recorder during SIDO 2022 with the participation of 4 key speakers from IoT world:
- Eric Faure : Responsable de l’équipe « Global Field Engineering », ProvenRun
- Frédéric Piller : Digital Factory R&D Manager, LACROIX
- Bruno Mussard : Security Marketing Manager, STMicroelectronics
- Laurent Denis : Marketing Manager – Microcontroller, Memory & Secure, STMicroelectronics
“Faced with the challenges of security and data protection for connected objects, an overview of recent solutions best suited to a given application” (replay in French)
More stories

Matter: everything you need to know about this protocol that could change the connected home industry

Electronic design: why an integrated design center can help you better develop your product

Electronic Design: A Winning Strategy to Accelerate Your Project Development

A successful IoT project: from CSR strategy to product development

